IRONKEY D300 Review: Why you want this hardware encrypted thumb drive, especially if you own cryptocurrency.
I was searching for a solution to store sensitive files without using the cloud.
My criteria were:
- Resistant to brute force attacks
- By default multiple failed passwords will wipe the device
- Resistant to bitwise imaging attacks
- If the device is out of your control for a short period of time, it is harder to create a bit-by-bit image of it in order to perform a brute force attack later.
- Physically robust
- Have no moving parts.
- I have seen models with integrated keypads, but moving parts can fail. You can mitigate keyloggers by using a virtual keyboard
- Water resistant and physically tough
- Stand up to day-to-day abuse
- Tamper resistant. It’s filled with resin. You cannot physically get to the components without destroying the device.
- Trusted manufacturer
- Kingston is a well-established player in the memory market
- Manufactured in the USA
- Standards-based
- Be compliant with NIST FIPS 140-2 Level 3
- This is the standard used for US Government to cryptographically secure data
- For more info: https://en.wikipedia.org/wiki/FIPS_140-2
- Be compliant with NIST FIPS 140-2 Level 3
- Compatible with different operating systems
- Able to be accessed from within Windows, MacOS, and Linux
- Support USB 2.0 or 3.0
- Have no moving parts.
What can be stored on these devices:
Cryptocurrency related files:
- Seed keys
- 2FA Private Keys and QR Codes
- Wallet.dat file backups
- Mining configuration and script file backups
- Transaction records
Personal files:
- Tax Returns
- Credit Card and ID card images
- Password database backups
- Other sensitive data
The IronKey D300
I chose the IronKey D300 (https://amzn.to/2ocYGMU) because it meets all of these criteria:

How to use your IronKey
Insert it into your USB slot:
Open the folder and choose the launcher for the appropriate operating system:
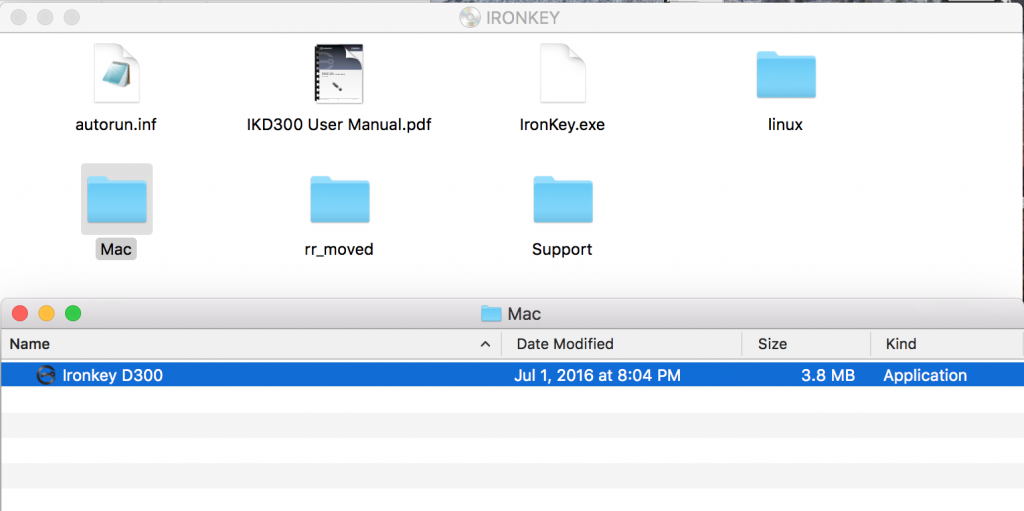
Type in your password and login:
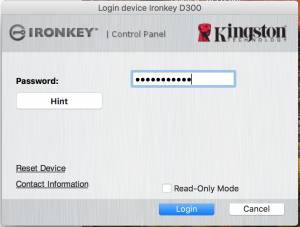
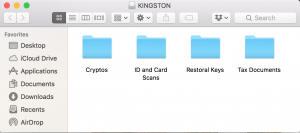
Open the newly appeared folder on your desktop:

Open the folder and copy your files:
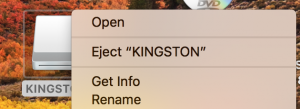
When you are done, simply eject the drive:
Recommendations
Virtual Keyboards
MacOS, Windows, and Linux all have virtual keyboards. You should always use one to defeat keyloggers. This will not defeat screen capture malware however. Use an air-gapped computer is possible for retrieving files. Otherwise, always keep your anti-malware software updated and use a firewall. You can also use a combination of physical and virtual keyboards to make the character correlation more difficult.

Here’s an example of the virtual keyboard within Mac OS High Sierra (System Preferences-Keyboard |Show keyboard and emoji viewers in menu bar)
Buy 2 of them!
Why you want two of these devices.
-
- Any hardware can fail. You’ll want to backup your data to something equally as secure.
- Keep one on your person, another in a safe
- Have the confidence to ditch or hide your device if under physical duress
- Your device could be unwittingly wiped by a household member
- Your device could intentionally be wiped by a would-be hacker
- This will require you to regularly synchronize the two drives. You can do this manually or using a file sync utility.
Lock and remove!
- Lock and remove your device after every use. An unlocked device can potentially be remotely accessed. Minimize the time window for which this can be accomplished.
Disadvantages
- They are expensive on a per GB basis. A normal 32GB USB drive costs about $10 USD. If you are looking to buy 2, you are looking at over $300. If you are protecting tens or hundreds of thousands worth of identity or financial data, this investment is small.
- There are export restrictions for hardware encryption devices in the US. You might not be able to purchase one if you are outside the US.
- They are larger and heavier than your average USB thumb drive
For more information:
https://www.kingston.com/datasheets/IKD300_en.pdf
To purchase:
At $156 dollars, the 32GB version is the best bang for your buck. Please consider using the following link to purchase:

